How IT Support Services Enhance Complete Cybersecurity
In today's digital era, the importance of cybersecurity cannot be overstated. Every business, regardless of its scale or field, faces an growing array of cyber threats that can endanger critical information, disrupt operations, and hurt standing. As cybercriminals become more sophisticated, it is crucial for organizations to focus on cybersecurity strategies to safeguard their resources and ensure business continuity. This is where outsourced IT solutions play a pivotal role, offering thorough solutions that improve overall cyber defense.
Managed IT services give businesses with the skill and resources essential to combat the most prevalent cybersecurity dangers, such as scams and ransomware threats. By partnering with a dependable IT managed IT services provider, organizations can benefit from preventive monitoring, cutting-edge security protocols, and customized guidance customized to their unique needs. Not only do these services help in protecting data and maintaining compliance with laws, but they also permit businesses to concentrate on their main activities while delegating the complexities of cyber defense to specialists. This partnership creates a solid fortification against cyber threats, allowing organizations to prosper in an increasingly connected society.
Grasping Cybersecurity Threats
Cybersecurity threats persist to evolve, presenting serious dangers to organizations of various sizes. These threats can vary from malware to phishing schemes, each taking advantage of different weaknesses within an organization's security measures. As discover this progresses, cybercriminals grow increasingly sophisticated, making it crucial for organizations to stay vigilant. Grasping the landscape of these threats is essential for implementing effective security measures.
One of the usual cybersecurity threats is a ransomware attack, a harmful program that encrypts a victim's data, asking for a ransom for decryption. Organizations can shield themselves from these types of attacks by keeping routine data copies and implementing strict control measures. Additionally, keeping applications current and educating staff about security best practices are crucial measures in minimizing the threat of ransomware attacks.
Another frequent threat is phishing, as attackers deceive people into giving up confidential information through fraudulent messages or texts. Spotting the indicators of a phishing scheme, such as incorrectly spelled domains or bad grammar, can assist employees not fall for becoming a victim of these threats. Implementing multi-factor authentication further protects critical information, as it provides an extra layer of security to access profiles. Comprehending these risks allows organizations to take preventive measures in safeguarding their important.
IT Administered Services Introduction
Information technology managed solutions refer to the practice of delegating your IT management and support to a external provider, allowing companies to concentrate on their core operations while ensuring that their technology infrastructure runs efficiently and safely. These services typically include a variety of offerings, such as network administration, security services, data backup and recovery, and cloud services, customized to meet the specific requirements of each company. By leveraging the skills of experts in the field, businesses can access cutting-edge tech and skilled personnel that may otherwise be too expensive.
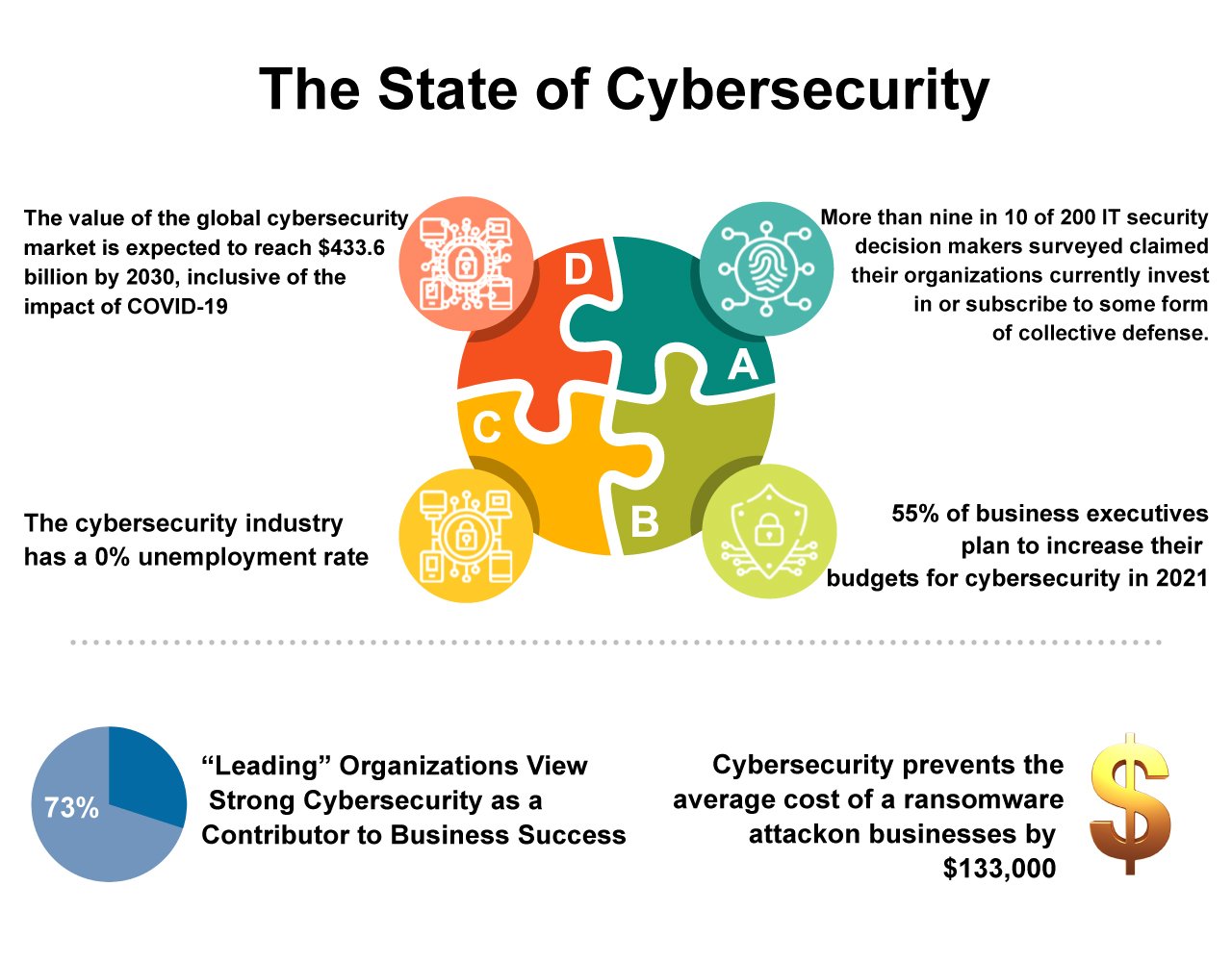
The benefits of IT managed services are substantial, particularly for businesses that require strong cybersecurity. With the growing prevalence of cyber threats, partnering with a managed services provider means having access to active oversight and immediate threat detection. This not only helps in avoiding online attacks but also allows for quick reactions in the event of a data compromise. Additionally, managed services providers often offer comprehensive compliance support, helping businesses navigate complex regulations such as HIPAA or the General Data Protection Regulation, which can be daunting for internal teams to handle alone.
In conclusion, IT managed services enable organizations to optimize their IT budget and resources, transforming fixed costs into consistent recurring costs. This cost-effectiveness, combined with the improved focus on security and compliance, positions managed services as a strategic path forward for businesses looking to thrive in an increasingly digital and threat-laden landscape. As tech continues to develop, so do these managed services, ensuring that businesses stay on top of new security developments and retain a market advantage.
Establishing Robust Cyber Defense Strategies
Creating robust cyber defense strategies is essential for every business aiming to shield its confidential information and ensure operational integrity. A comprehensive approach entails ongoing cybersecurity training for employees, making sure they are aware of the prevalent threats such as phishing attempts and social engineering attacks. Implementing training programs designed to educate staff on how to identify and prevent these threats can substantially reduce the risk of being compromised to attacks. Additionally, fostering a culture of security awareness helps forge an environment where each employee understands their role in safeguarding the organization.
Utilizing cutting-edge technologies is an additional key element in a successful cybersecurity strategy. This includes the deployment of multi-factor authentication, encryption methods, and device protection solutions that help secure technology used by employees, particularly in telecommuting work settings. By embracing these technologies, businesses not only enhance their security posture but also ensure compliance with regulations such as HIPAA and GDPR. It is imperative to ensure these systems maintained and to conduct regular risk assessments to identify vulnerabilities and areas for improvement.
Finally, businesses must develop a comprehensive incident response plan to address potential cyberattacks successfully. This plan should specify the steps to take in the event of a data breach, including roles and responsibilities, communication strategies, and recovery processes. Conducting routine drills to test this plan guarantees that the team is prepared to respond quickly and effectively, lessening the impact of an attack. Furthermore, partnering with an IT managed services provider can enhance these strategies by providing expert guidance, ongoing monitoring, and support to adapt to the evolving landscape of cyber threats.